
How to Set Up Role-Based Access in Salesforce
Anisha
As per a report by Varonis, 58% of organizations experience insider threats or data breaches caused by mismanagement of access permissions.
However, the risk of improper access is broader than just security. It can also lead to:
- Operational inefficiencies
- Compliance violations
- Company reputation damage
Managing who can view, edit, or share sensitive information is one of the biggest challenges for businesses, especially when using platforms like Salesforce.
With data being increasingly dispersed across various teams, setting clear access boundaries is vital for maintaining smooth workflows and ensuring regulatory compliance.
This is where role-based access (RBA) comes in. By assigning permissions based on roles, Salesforce enables you to control data access effectively.
Additionally, RBA streamlines your internal operations by ensuring employees only access the data they need to perform their job functions, reducing unnecessary distractions and increasing productivity.
This approach also minimizes the chances of human error, further securing sensitive data and avoiding costly mistakes.
That being said, let’s explore the step-by-step process of setting up role-based access in Salesforce.
What Is Role-Based Access in Salesforce?

Role-based Access in Salesforce is a permissions model that allows organizations to manage data access by linking permissions to predefined roles rather than individual users.
Unlike traditional access management systems, where permissions are manually assigned to each user, RBA assigns permissions based on an individual’s role within the organization.
This approach streamlines operations by aligning access to data with organizational hierarchies and departmental structures.
For example, sales teams may need access to customer data, while finance teams may require access to financial reports, but both roles should be distinct regarding data access.
Salesforce's flexible framework allows you to customize these roles and permissions to suit your organization’s structure, helping you manage user access even as your company scales or undergoes organizational changes.
This approach ensures your system remains efficient and secure as your business grows, adapting to new needs without compromising data safety.
What Are the Benefits of Role-Based Salesforce Access?

With insider threats causing a majority of cyberattacks and costing businesses millions, managing who can access your data is highly critical.
Salesforce’s Role-Based Access offers a robust solution to mitigate these risks while improving overall operations.
Here are the key benefits of implementing RBA in Salesforce:
-
Enhanced Data Security
RBA prevents unauthorized access by ensuring employees only see the data necessary for their roles. Sensitive information remains protected, reducing the risk of data breaches.
-
Improved Operational Efficiency
By tailoring access to each employee's responsibilities, RBA eliminates unnecessary distractions and ensures teams can focus on what matters.
-
Compliance and Audit-Readiness
RBA simplifies compliance with regulations like GDPR and HIPAA. Businesses can easily track and document audit permissions by limiting access to sensitive data.
-
Reduced Risk of Human Error
Restricting access reduces the chances of accidental data alterations or mismanagement, safeguarding your critical business information.
-
Scalable Access Management
With the flexibility to adjust permissions based on evolving business structures, RBA can easily accommodate new hires, department changes, or evolving responsibilities. This scalability ensures efficient data access management, even as teams expand or restructure.
-
Better Data Segmentation for Targeted Analysis
Using RBA, you can better segment data access according to specific roles, enhancing data analysis and reporting.
By aligning access to these needs, Salesforce users can pull relevant, role-specific insights, driving more accurate and actionable data analyses.
-
Streamlined Onboarding Process
Administrators can quickly set up access rights that align with their job responsibilities by assigning predefined roles to new hires.
This eliminates delays caused by manually reviewing employee access rights and ensures new users access the right resources from day one.
-
Improved Collaboration Across Teams
When employees only see the data relevant to their roles, they can focus on their tasks while respecting privacy and confidentiality.
At the same time, RBA makes it easier to share insights across teams without exposing sensitive information, promoting interdepartmental cooperation and enhancing overall workflow.
-
Reduction in IT Burden and Costs
By automating access control based on roles, RBA reduces IT teams' need to manage individual permissions manually. This saves time and reduces the risk of errors caused by manual configurations.
As a result, IT resources can be allocated to more strategic tasks, leading to cost savings and improved operational efficiency.
Step-by-Step Guide to Setting Up Role-Based Access in Salesforce
Implementing role-based access in Salesforce requires a systematic approach to ensure data security and operational efficiency.
Here's a detailed, step-by-step guide to get you started:
Step 1: Define Your Data Access Requirements
The foundation of role-based access begins with identifying and categorizing your data to ensure that sensitive information is protected while aligning with operational needs.
-
Identify Critical Data Points
Begin by evaluating your Salesforce instance and pinpointing sensitive data, such as customer records, financial reports, contracts, and proprietary business insights. These critical assets need strict control over who can access, edit, or share them.
-
Classify Data by Sensitivity and Relevance
Organize your data into categories based on its level of sensitivity and relevance to specific roles. This classification will help you assign appropriate access, avoiding both over-permissioning and under-permissioning.
For instance:
- High Sensitivity: Financial records, client contracts, legal documents.
- Moderate Sensitivity: Sales pipelines, customer leads, internal workflows.
- Low Sensitivity: General marketing materials, non-critical resources.
By organizing data into these categories, you ensure each role has access only to what is essential, reducing unnecessary risks.
Step 2: Map Out Your Role Hierarchies
A clear understanding of your organizational structure is essential when setting up access permissions.
-
Understand Your Company’s Structure
Document your company’s departments, teams, and reporting relationships. Identify which roles require access to specific data and understand the extent of that access.
Example roles include:
- Sales Managers need access to their team’s leads and opportunities.
- Finance Teams require access to financial reports and budget documents but not to client-specific data.
-
Create a Role Hierarchy in Salesforce
Salesforce allows you to create role hierarchies that map to your organizational chart. Begin by replicating this hierarchy in Salesforce to set the scope of each role’s data access. For example:
- Top-Level Roles: CEO and senior management with access to all data.
- Mid-Level Roles: Department heads, such as Sales Directors, with access to their team's data.
- Entry-Level Roles: Sales representatives or analysts with limited access based on their tasks.
The role hierarchy feature in Salesforce ensures that higher-level roles automatically gain visibility into records owned by their subordinates.
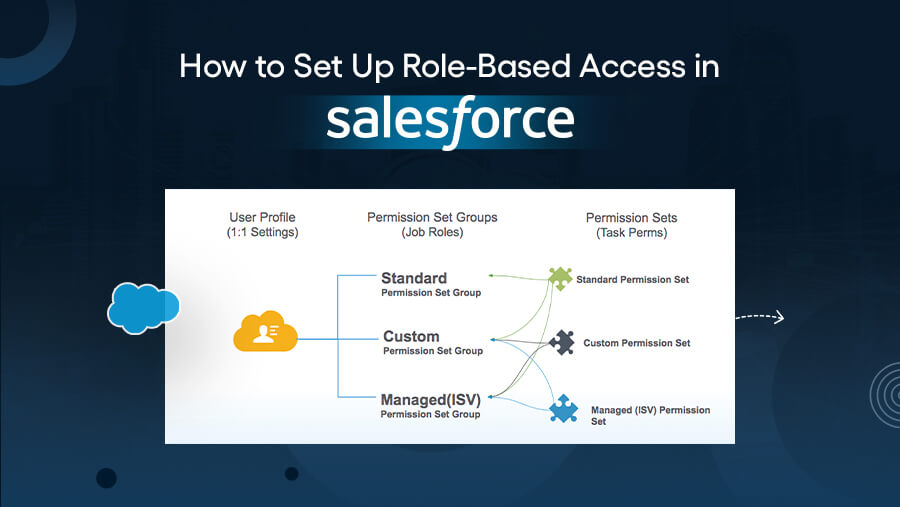
Step 3: Assign Roles and Permissions
Once you’ve established your roles and data access requirements, it’s time to assign permissions.
- Use Profiles to Set General Permissions
Profiles control baseline access for users. For example:
- A Sales Profile might allow access to leads, opportunities, and basic customer information.
- A Finance Profile may allow access to invoices, financial reports, and account details but exclude customer-specific records.
-
Leverage Permission Sets for Additional Access
Permission sets offer flexibility by allowing you to extend access to additional features or records without modifying a user's profile. This is especially useful for granting temporary or one-off permissions. For instance:
- A sales rep with a basic profile might need temporary access to specific financial reports. You can grant them a read-only permission set for the project's duration.
- Example Use Case: Assign read-only access to finance reports for sales teams, ensuring they can view but not alter sensitive financial data.
Using permission sets provides flexibility while maintaining security.
Step 4: Configure Sharing Settings
This step ensures your access permissions align with your broader security policies and organizational needs.
-
Set Org-Wide Defaults (OWD)
The OWD setting defines baseline access across your Salesforce organization. You can set these defaults to control how records are shared:
- Private: Only record owners can access their data.
- Public Read-Only: All users can view data but not edit it.
- Public Read/Write: All users can view and edit data.
For example, set customer records to Private while keeping general product information Public Read-Only to allow all users to view product details without editing them.
-
Use Role Hierarchy Settings
Salesforce’s role hierarchy ensures that higher-level roles can access records owned by those beneath them in the organizational structure.
For example, a department head can automatically access all records their team members own. This enables streamlined access while respecting the organizational hierarchy.
-
Explain Manual Sharing
In some cases, you may need to share records on a case-by-case basis. Salesforce offers Manual Sharing to give specific users access to records outside of their regular access. This is ideal for situations such as:
- Sharing a contract file with a legal team member for review.
- Granting temporary access to a marketing consultant to view sales data.
Manual sharing provides a flexible, one-time solution for unique access needs.
Step 5: Test and Review Access Levels
Once you’ve configured roles, profiles, and permissions, testing is essential to ensure everything functions as expected.
-
Conduct Role-Based Testing
Test each role to verify that permissions are correctly applied. Have users from different roles simulate their day-to-day tasks to check for access gaps or overlaps. For example:
- A sales manager should be able to view their team's leads and opportunities but not have access to sensitive financial data.
- A customer support agent should be able to view customer interaction history but not modify financial records.
Testing helps identify potential issues and ensures that each role has the right level of access.
-
Regularly Audit Access Logs
Ongoing audits are crucial for maintaining security and ensuring your access policies are followed. Regularly review access logs to detect unusual activity, such as unauthorized attempts to view or modify sensitive data.
This proactive approach helps ensure that any discrepancies are quickly addressed.
-
Update Roles and Permissions Periodically
As your organization grows, roles, teams, and responsibilities may evolve. Periodically review and adjust access settings to reflect these changes. Ensure your permissions align with current business needs and compliance requirements.
Pro Tips to Ensure Effective Role-Based Access Management
Here are actionable tips to help you effectively manage and optimize role-based access in Salesforce:
1. Regularly Audit and Update Roles
Conduct periodic reviews of roles and permissions to align with team changes and evolving responsibilities.
2. Document Roles and Permissions
Maintain clear documentation of your role hierarchies and associated permissions for easy reference and faster troubleshooting.
3. Train Employees Regularly
Educate your team on safeguarding data and adhering to access protocols to minimize insider threats.
4. Avoid Common Mistakes When Setting Up RBA
-
- Over-Assigning Permissions: Granting excessive access increases the risk of data exposure.
- Neglecting to Review Roles: As teams grow or change, outdated roles may lead to security vulnerabilities.
- Forgetting Least Privilege Principles: Always grant the minimum access required for a role to perform its job effectively.
Conclusion
Implementing role-based access in Salesforce is key to safeguarding sensitive data and boosting operational efficiency. Controlling access based on roles can enhance security, streamline workflows, and ensure regulatory compliance.
Ready to optimize your Salesforce environment? Let’s talk about how to protect your data and improve team productivity!
News Letter
Subscribe our newsletter to get our
latest update & news


